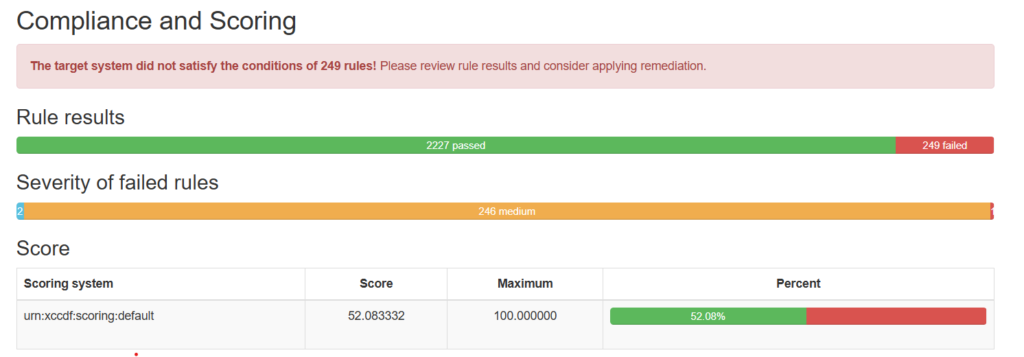
Overall Security Posture: Moderate Risk
The baseline assessment identified 249 configuration gaps, primarily of medium severity, indicating opportunities to improve system hardening, logging, and access controls.
No critical systemic failures were observed; however, several controls require remediation to meet industry and regulatory expectations.
Compliance Framework Coverage
PrimeNexus assessments map technical findings across multiple regulatory and security frameworks, allowing a single remediation effort to address overlapping compliance requirements.
| Framework | Coverage |
|---|---|
| CIS Oracle Linux 8 | System hardening baseline |
| DISA STIG (OL8) | Defense-grade security controls |
| NIST SP 800-53 | Risk and control alignment |
| PCI-DSS (where applicable) | Regulated environments |
A single technical finding may satisfy requirements across multiple frameworks.
Want a report like this? Explore our security compliance services.
🔴 Finding ID: PN-AC-001
Title: Prevent Login to Accounts With Empty Passwords
Severity: High
Status: Failed
Category: Access Control
Control Source: CIS / STIG / OpenSCAP
Affected System(s): Oracle Linux 8
📌 Summary
The system permits authentication for user accounts without enforced password requirements. This weakens access controls and significantly increases the risk of unauthorized system access.
💼 Business Impact
If left unaddressed, this issue may result in:
- Unauthorized or anonymous system access
- Violation of security baseline and compliance requirements
- Increased audit findings and remediation effort
- Potential lateral movement during a security incident
⚙️ Technical Details
OpenSCAP detected that the system configuration allows user accounts with empty or null passwords to authenticate, which violates secure authentication practices.
Detected by: OpenSCAP (SCAP Security Guide – OL8)
Rule ID: xccdf_org.ssgproject.content_rule_no_empty_passwords
Result: Fail
🛠️ Recommended Remediation
- Disable empty-password authentication in PAM configuration
- Identify and lock or remediate affected user accounts
- Enforce password policies across all local accounts
- Re-run compliance scan to validate remediation
📊 Compliance Mapping
| Framework | Control |
|---|---|
| CIS OL8 | 5.4.1 |
| DISA STIG | OL08-00-020331, OL08-00-020332 |
| NIST 800-53 | IA-5 |
🧠 Consultant Note
This issue is typically quick to remediate but represents a high-impact access control weakness. Addressing it early significantly reduces both breach risk and audit exposure.
📸 Evidence
Figure: OpenSCAP assessment output showing failure of the “Prevent Login to Accounts With Empty Passwords” control.

What You Receive From a PrimeNexus Assessment
Versioning Notice
PrimeNexus aligns findings to current security frameworks while maintaining version awareness across evolving standards. Control identifiers and mappings are aligned to the applicable benchmark and framework versions in effect at the time of assessment. Section numbers and control references may vary across framework releases.